Microsoft Security Fundamentals (Draft)
Security Layers
Security Principles
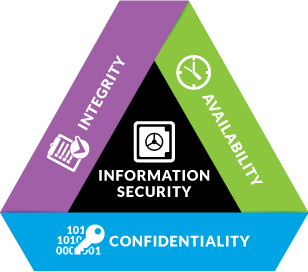
Information Security is built up with the three prinicples;
Confidentiality
To ensure information is secure from unpermitted users.
Integrity
To ensure that data is correct and accurate fr its intended purpose.
Availability
To ensure data is avaliable at the right time.
Managing risks is extremely important for any organisation, having a management plan in place will help prevent and remove possible risks in the future.
Using a risk matrix can help identify the likelihood and the consequence of a risk.
A rule that is crucial to follow is the "principle of least privilege" (POLP), giving the user the basic level of access to information and resources they need to forfill their jobs.
It is imporant to have all outbound and inbound traffic to be denied and only allowed if it has been requested and appropriate justification.
Social Engineering
Social engineering - Is to manipulate people to perform tasks to allow the attacker to gain access to sensitive information.
Man-In-The-Middle
A Man in the middle attack (MITM) - is a type of attack that intercepts traffic without the user knowing. When a request is sent, a source and destination MAC address is used, as it is hardcode (unique). An ARP table is used to place an IP address to each MAC address, a man in the middle attack consists of changing the ARP table by replacing the router MAC address with the attackers MAC address, thus intercepting the traffic.
Defence in Depth
Defence in Depth - is a concept of having multiple layers of security, this counts for both technology controls and people. The solutions for Defence in Depth can include; firewalls, IDS, IPS, DMZ.
Microsoft Software
Microsoft Baseline Security Analyzer - is a piece of software that will detect any missing security updates and security misconfigurations.
Microsoft Security Compliance Manager (SCM) - is a tool to configure nad manage computers in an enviroment ad prviate cloud using group policy.
Physical Security
Keyloggers - is a type of device that can be inserted into the computer to capture keystrokes, this is extremely effective to capture users login credentials.
Access Control - restricting access to individuals to the resources that are permitted.
Two factor Authentication (2FA)
Is a process of adding another layer of security. An example would be to login with your user name and password and then requiring you to then enter a code that has been sent to you over SMS (text).
Mobile Devices
portable devices have three issues, them being loss, left and espionage.
a docking station is one way of keeping a device physically secure, allowing the user to lock it to the dock to prevent a user to steal the laptop.
Encryption is another layer of security, if a device has been stolen. Preventing users access information stored on the device.
Internet Security
ActiveX
is technology to allow to code and run it in IE, this can be harmful as someone can add malicous code (e.g. spyware). Its normally blocked.
Java
java can be dangerous as it can be java applets that can installed spyware or viruses.
Plug-ins
Plugs can offer the same risks, being exposed to spyware or viruses.
Zones
There are four zones; Internet, Local Internet, Trusted site and Restricted sites. You can click on a zone and customise on what is enabled and disabled, e.g. ActiveX and Java.
Wireless Security
Wireless networks have disadvantages be easily interpected compared to wired connections. It is also easier for individuals to spot a network that is close by, this can be seen via the SSID (Name of the network). You can alternativly hide the SSID to prevent individuals from see tthere is a network close by.
When choosing a wireless protocol it is advised to use WPA2, as it is the most recent and secured network.
Wireless access points normally allow you to use one frequence, however some can allow two which are 2.4GHz and 5GHz. This can allow old technologies to connect to the acces point as they may not be compatible with 5GHz. 2.5GHz is primarily for long distance, but longer download and upload speeds with 5GHz is for a shorter distance with faster download and upload speeds.
Most wireless access points can have the SSID disabled, although this makes it harder for users to connect, but helps increase the security.
Organisations can implement a RADIUS server that will help he wireless access point authenticate users connecting to the access point, checking with the radius server on whether it should like that person connect to the network.
MAC address filtering can be used, allowing you to hardcode a list of devices that can connect to the network.